We've seen a lot of attempted spoof emails recently and recommend checking SPF, DKIM, DMARC and MTA_STS settings to protect your domain.
Here are googles recommended settings to help prevent spoof emails coming through to the school.
Googles help article
First, ensure mail delivery & prevent spoofing with SPF record
SPF lets you specify the servers and domains that are allowed to send email for your organization. When receiving mail servers get a message from your organization, they compare the sending server to your list of allowed servers. This lets receiving servers verify the message actually came from you.
If you are using gmail for emails this is the txt record to add to your DNS:
txt record name:
@
txt record value:
v=spf1 include:_spf.google.com ~all
Then increase security for outgoing email with DKIM record
DKIMs adds an encrypted digital signature to every message sent from your organization. Receiving mail servers use a public key to read the signature, and verify the message actually came from you. DKIM also prevents message content from being changed when the message is sent between servers.
Just contact realsmart support and we will supply you a txt record to add to your DNS
Enhance security for forged spam with DMARC record
DMARC: Lets you tell receiving servers what to do with outgoing messages from your organization that don’t pass SPF or DKIM checks
Your DMARC policy is defined in a line of text values, called a DMARC record. The record defines:
• How strictly DMARC should check messages
• Recommended actions for the receiving server, when it gets messages that fail authentication checks,
Have a read of this page it explains all the tags, what they mean and the settings:
Here is an example DMARC record that another school uses:
TXT record name:
_dmarc.yourgoogledomain
TXT record content:
v=DMARC1; p=quarantine; rua=mailto:an email group or user at your school; adkim=r; aspf=r
v=DMARC1 is required and just tells the DNS which dmarc version is being used
p=quarantine means any messages affected will be treated as spam and send it to the recipient's spam folder. Recipients can review spam messages to identify legitimate messages.
rua=mailto:an email group or user sends reports to the email address
adkim=r sets a relaxed policy for any message affected by DKIM records
aspf=r sets a relaxed policy for any message affected by SPF records
1st place to start is create a group that you want to receive the report emails and how you want to treat affected emails- we suggest Quarentine
MTA-STS to protect the privacy of your emails (security and anti-spoofing)
The objectives of MTA-STS are to:
- make it harder for an attacker to get emails sent to an alternative location
- make sure that TLS encryption is always used; to prevent attackers downgrading email encryption on emails to clear text.
MTA-STS is relatively simple to implement, but organisations must step through their implementation with care; if you switch on controls too quickly then inbound emails won’t be delivered. To mitigate this risk, we always recommend using MTA-STS in ‘testing mode’ first, and to set up TLS-RPT (TLS Reporting) as well, which is a mechanism for getting feedback before you progress.
Google make it realy simple for you.
- Sign into google admin
- Create a google group called smtp-tls-reports and add the users that you want to recieve reports.
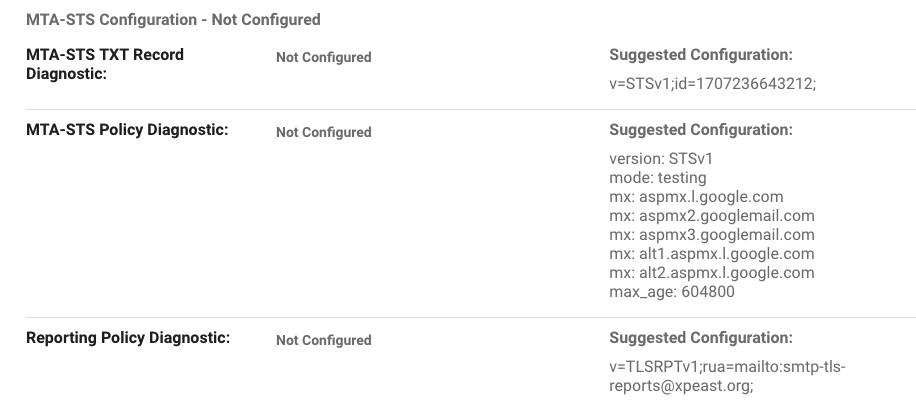
- Check the MTA-STS configuration for your domain- are there already txt records in place called _mta-sts.your-domain and _smtp._tls.your-domain if so MTA-STS has been set up by someone else.
- Check MTA-STS status and get suggested configurations from google here:https://admin.google.com/ac/apps/gmail/compliance
- Scroll to bottom of the page and hit 'Validate your MTA-STS'
- You will see all of your domains listed and the status of each domain MTA-STS
- google will give you the DNS txt settings for _mta-sts.your-domain and _smtp._tls.your-domain they will look something like this:
- Create an MTA-STS policy. You'll see the suggested Configuration in screenshot above says mode:testing we recommend testing and check reports for 5-10 days then changing the Policy to be mode:enforced
- Publish the MTA-STS policy:
create a txt file with the configuration as googles recommendation e.g.
version: STSv1mode: testingmx: aspmx.l.google.commx: aspmx2.googlemail.commx: aspmx3.googlemail.commx: alt1.aspmx.l.google.commx: alt2.aspmx.l.google.commax_age: 604800
Add the policy to a web server in your domain
Verify that your domain is set up with a public web server.
Add a subdomain to your domain. The subdomain name must start with mta-sts, for example:
mta-sts.your-domain.com
Create a directory named .well-known in the subdomain.
Upload the policy file you created to the .well-known directory.An example URL for an MTA-STA policy is:
https://mta-sts.your-domain.com/.well-known/mta-sts.txt - Add DNS TXT records to turn on MTA-STS and TLS reporting.
e.g. txt record called _mta-sts pointing at v=STSv1;id=12345678;
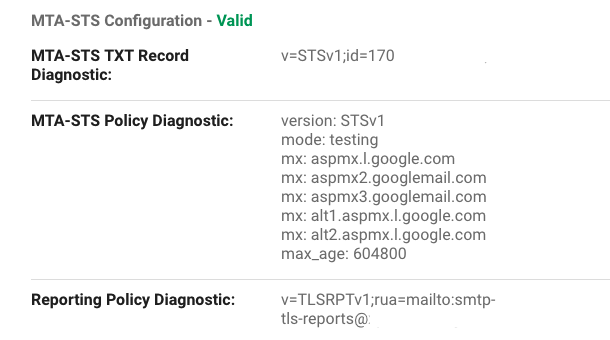
and txt record called _smtp._tls pointing at v=TLSRPTv1;rua=mailto:smtp-tls-reports@your-domain.com; - Once you are all set up navigate back to https://admin.google.com/ac/apps/gmail/compliance and hit 'Validate your MTA-STS configuration here.'
- Select your domain and check that MTA-STS Configuration - says Valid as screenshot.
- MTA-STS is now in place. Check emails for reports and remember to change the txt file to mode:enforced after testing